Migration of ATS8300 to ATS8600
Migration of ATS8300 to ATS8600, what are the characteristics of individual systems and how the migration process works.
Shortcuts:
-
About ATS 8300
-
About ATS 8600
-
Architecture of the Advisor Management ATS 8600 system
-
ATS8600 – user interface
-
Users
-
Monitor capabilities
-
How licensing works
-
SKD access control controller – ATS1250 selected
Migration of ATS8300 to ATS8600
About ATS 8300
Alliance 8300 is a security system client-server management application with LAN or WAN communication capability.
Professional – Serwer Alliance 8300Professional server components:
Alliance 8300 Client – PCClient computer components:
|
|---|
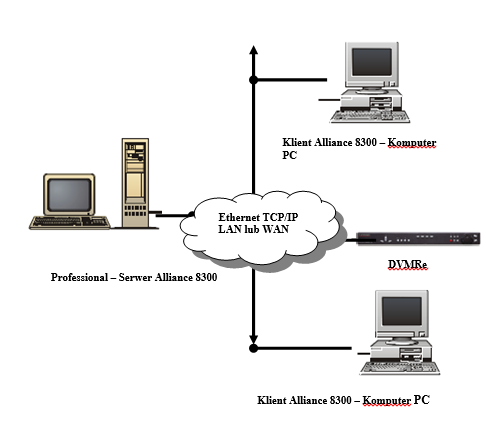
Professional Alliance 8300 server with two remote clients and digital video recorder
The ATS 8300 system is no longer offered for sale. Existing installations are recommended to be rebuilt and adapted to the new system that is the successor of the ATS 8300, i.e. the Advisor Management Software ATS 8600.
About ATS 8600
The Advisor Management application – in the commercial offer as a product with the symbol ATS8600 – is intended to support most devices produced by UTC F&S (currently Carrier Company):
- central SSWiN i SKD ATS Master,
- central SSWiN i SKD Advisor Advanced,
- central SSP FP1200 i FP2000,
- central SSP family 2X and Kilsen KFA,
- recorders VSS/CCTV with analog cameras, digital cameras IP and hybrid from TruVision.
ATS8600 uses typical database solutions. In the case of small and medium-sized systems – the default SQL MS SQL 2012 express edition database. In larger systems, you can use the MS SQL 2012 or MS SQL 2014 Standard Edition database installed on the same server or another device, as well as the available mechanisms and tools for database maintenance. If encryption of the communication between the client station and the server is required, this can be easily enforced by setting the SSL encryption of the secure network connection protocol.
The application is available in several license options, depending on the required number of supported devices:- ATS8600 Starter Edition – support for up to 2 devices of each category (ATS Classic control panels, Advisor Advanced control panels, VSS / CCTV recorders, SSP control panels,
- ATS8600 Business Edition – support for up to 25 devices from each category.
It is also possible to flexibly create additional licenses, e.g. after exceeding 25 devices in any category.
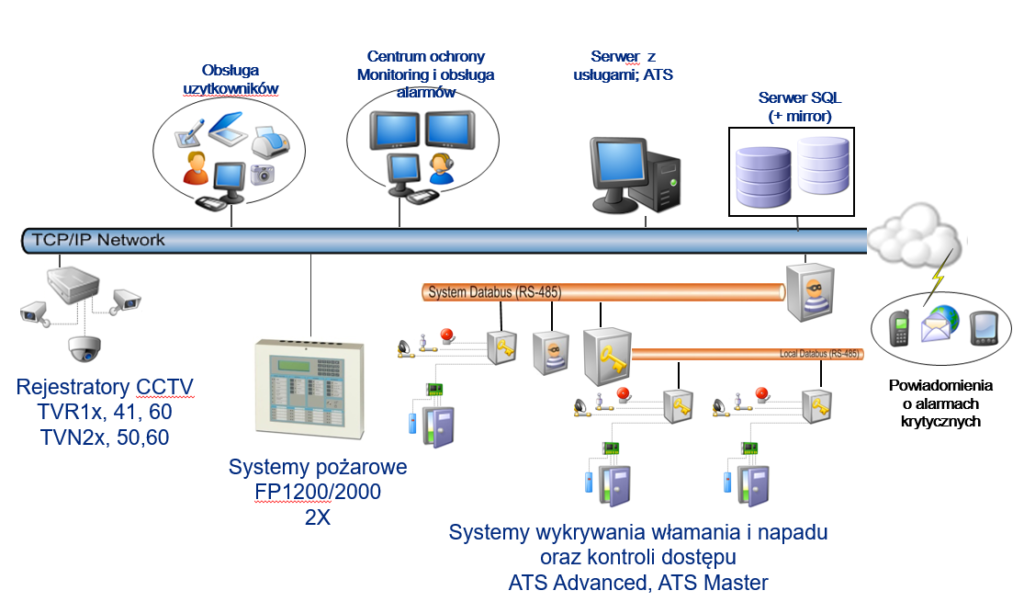
Architecture of the Advisor Management ATS 8600 system
What is Migrating ATS8300 to ATS8600?
The ATS8600 has built-in hardware configuration loading tools.
The migration of ATS8300 to ATS8600 is therefore the transfer of the list of users by exporting / importing the database to external files. Other operations should be performed from scratch, especially the user structure and authorization structure, visualization, automatic actions, event handling scenarios, operator environment, etc.
ATS8600 –GUI
|
The ATS8600 application is constantly developed and improved. The modern application interface is visible next to it. The interface is clear, intuitive to use and user-friendly. The application works in Polish or another language (English in the photo) |
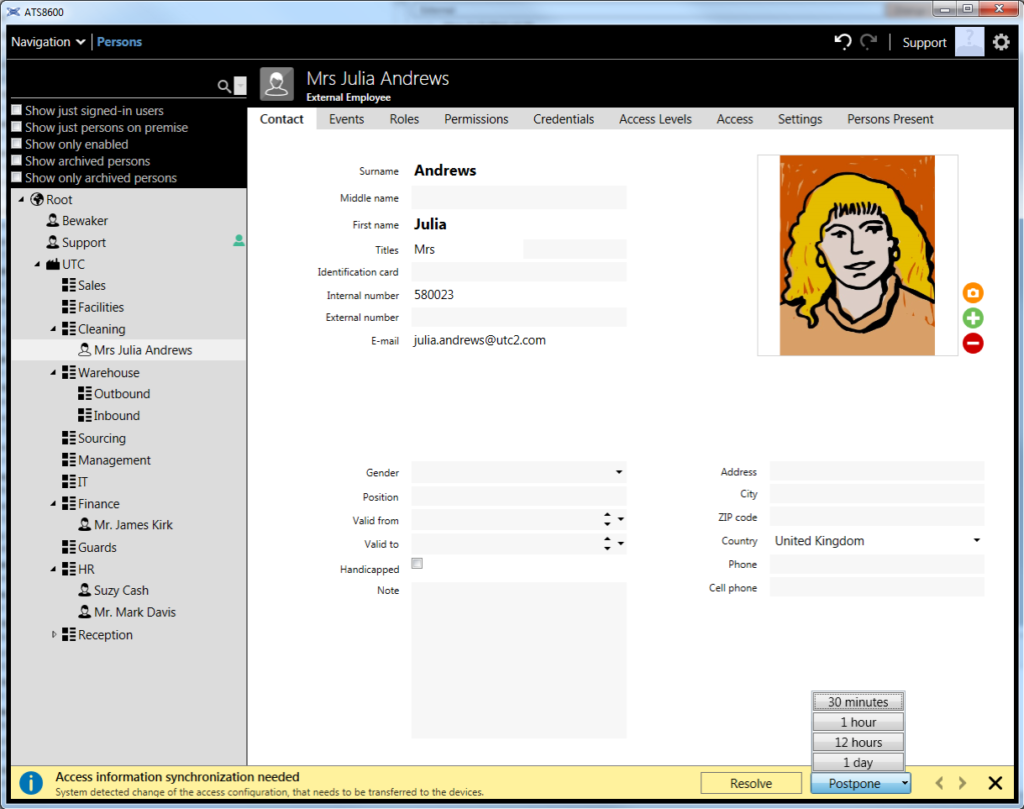 |
|---|
Navigation is used to conveniently navigate through the application and switch between different program locations.
ATS8600 – user interface
Architecture
- The menu navigation for navigating through the program
- < Tabs provide various elements or properties about the node/li>
- A node is one object in a structure (e.g. one person or one department or one device)
- The list of objects of the “tree” type presents information in a hierarchical structure (people, devices, regions), in which related items are interrelated:
- Parent object: an object that contains 1 or more elements
- Child object: an object that is contained in (or belongs to) a parent object
- A child object can also be a parent of the items below it
- The notification bar is displayed automatically to help you take immediate actions, e.g. informing about the need to send data to panels or handling an alarm event
Users

People, regions and devices are presented in an ordered list with a hierarchical tree structure. A solution of this type makes it easier to view and manage the most complex structures.
Persons- Application users
- System users
- Hardware architecture
- Logical ordering of the object

There is no key responsible for saving the edited data in the application. The data is saved to the database on an ongoing basis, this is due to the fact that many users can work on a common database. In case of a mistake we can use the undo / redo keys.

Filtering makes searching easier and reduces the number of items in long lists
- It allows you to search in all fields, just enter (part of) the value to filter
- Capitalization does not matter
- To filter on a specific field, enter: [field name]: value
- Use quotation marks if the value or field name contains white space or punctuation marks
- Example “zip code”: “1234 ABC”.
- Combining different fields: “zip code”: “1234 ABC” “e-mail”: utc
Monitor capabilities
- Viewing and handling events and alarms
- View information about an event
- Observation of the current situation in the facility
- Device control
- Locating alarms
- Sound notifications
How licensing works
- It allows you to activate communication with the licensed device
- Each device (driver – active connection) requires a license
- In a closed-circuit television system, each recorder camera requires a license
- In the fire alarm system of the SSP, each node requires a license (control panel and repeater)
- No license is required to configure device structures, people, access levels, etc.
- A license for client stations is not required
- The ATS8600 and ATS8610 licenses cover a maximum of 2 or 25 devices of different types
After selecting the device position from the navigation, we will switch to the view that allows you to manage the hardware structure of our system.

SKD access control controller – ATS1250 selected |
|
|---|
The persons in the ATS8600 system are described in the “Personal data” tab by:
- Name
- Name
- Extension
- Picture
- System identifier
- Card
- Pin code
- Access rights
- We define the ability to move around the facility
- Roles
- We define the access rights to the ATS8600 application
People functions in the ATS8600 system:
- Differences in persons:
- Access level
- Roles
- Icons:
- Manager (appears at the top of the list)
- Person (displayed right behind the manager)
- External worker (displayed last)

- Defines rights for users related to areas, access to doors and floors in the facility (physical access rights)
- People in levels can be added individually
- May contain schedules
Role
- Roles define the permissions for the user of the ATS8600 application
- Includes permissions for menus, devices, access levels, users, etc.
The tree structure groups people according to their organizational affiliation
- The highest node is Root (default name can be changed)
- is responsible for companies (at least one is required)
- People are assigned to organizational units:
- company: the highest level
- Branch: Sub-level of the company
- Center: Sub-level of the company or division
- DepartmentSub-level of a company, branch, or center
Hierarchical structure
|
|---|
Bookmarks:
- Contact – basic information: personal data, address details, photo
- Events – list of events related to the indicated person
- Roles – ATS8600 operator authorization set
- Permissions – define ATS8600 functions available to the operator
- Cards / PINs – a list of issued identifiers and operator login and password
- Access levels – access levels assigned to a person
- Access – Access rights to specific doors and areas
- Settings – program operator preferences, eg application language
Adding a new person
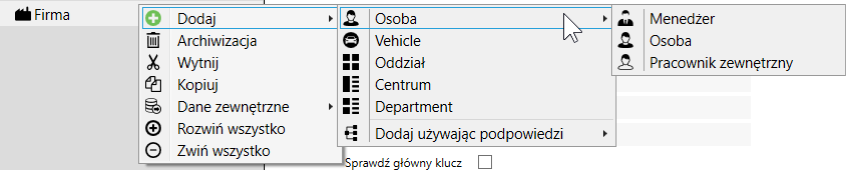
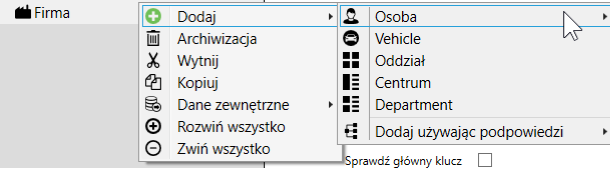
Adding a new person
- Click with the right mouse button on the selected organizational unit
- Select “Add”> “Person”
- Manager
- Person
- External worker
- Complete data
- Required fields marked in red
- Add a photo (photo import) supported png, jpg and png formats
- Give permission
- Add identifiers
Importing people
- Adding users to the system using import is a very helpful tool
- In the case of adding a large number of people, we can prepare / format an appropriate * .csv file ourselves
- Importing can often help migrate from Titan or Alliance systems
- Titan2CsvExport is used to export users with cards from the Titan program, and the AllianceAtsToAdvisorManagment application
- We can also export a * .csv file with user data from the ATS8500 program
- PIN codes cannot be imported as they would become explicit in the * .csv file
- The * .csv file allows for any data editing before importing (e.g. we can add internal numbers to users or complete personal data)
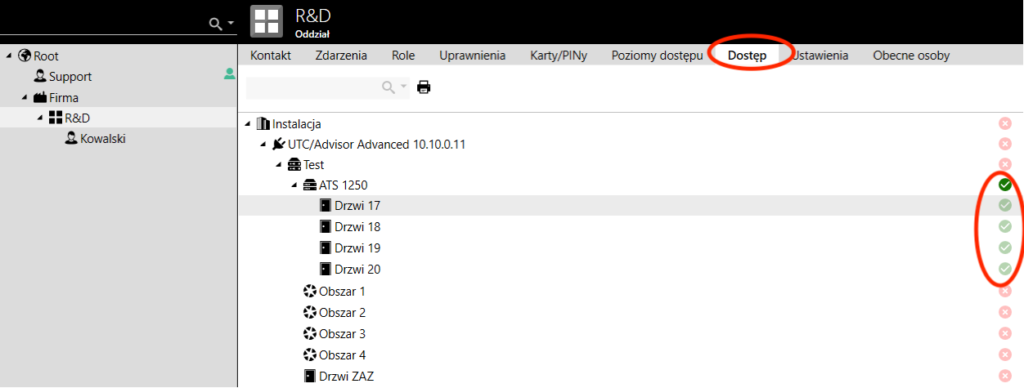
A simple method of granting access
Select “People” from the navigation:
- We select the parent node
- Go to the “Access” tab
- We grant appropriate access rights
- Access rights are inherited to the child nodes (in the figure below, access rights have been granted in the door controller, so each door has inherited access)
 |
 |
|---|

There are two methods of assigning access rights:
- Simple: access 24 hours a day
- Advanced: access based on “access levels” based on schedules, introduces order, ideal for complex projects, this method is recommended
Select “Access levels” from the navigation:
- Access levels allow for detailed configuration of the user level (this can be compared to the alarm group settings in the Master system or the user group in the Advanced system)
- Use the (+) icon to create a new access level, and then the (-) icon to delete the existing one
- To make the configuration easier, by right-clicking, we can choose the duplicate access level options
 |
 |
|---|
Alarm management and handling:
- Effective alarm monitoring
- Quickly define the place of the event
- Information about forcing the door / door open for too long
- Multiple event handling (queuing)
- Acknowledging events and resetting alarms
- Fast and effective response
- Overview of related events, live or in history
- For the correct localization of alarms it is necessary to configure:
- Regions
- Assign devices to regions


In an alarm monitor, region, event, and alarm tabs can be detached from the home screen and spread across multiple monitors. Thanks to this, we gain more space, and the map with the visualization of the object can become very large, the operation of the system is easier and more convenient.
The universality of the application is based on the fact that events can be found not only in the monitor, but also in devices, regions and people. A special icon will allow you to view events from the current or current node and its subordinate nodes.
 |
 |
|---|
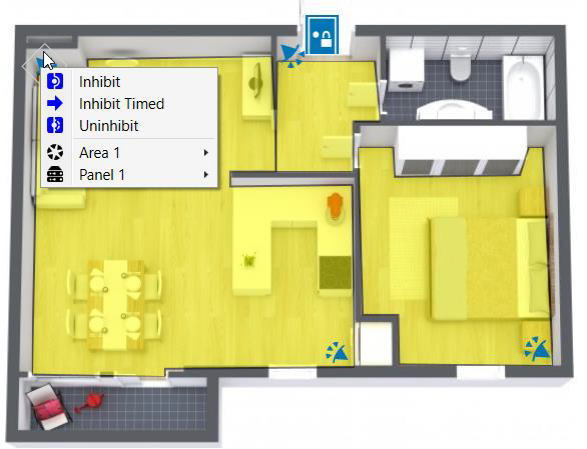
Controlling devices
- Select the device from the map
- Click the mouse button to select available commands from the context menu
- Master nodes can also be given commands
 |
 |
|---|
Firma KARO Karlicki Sp. z o.o. company offers its assistance at every stage of the migration from ATS 8300 to ATS 8600, starting from the initial analysis of the situation, through reconnaissance on the site and smooth migration to the new system. If you have any questions, please do not hesitate to contact us.
Our employees are well trained, they have proper knowledge, experience and required permissions.
We invite you to cooperation.